Solving Spectre and Meltdown may ultimately require an entirely new type of processor - ioriomemmar
How to identify and fix execution bugs like Spectre and Nuclear meltdown has been a burning topic among microprocessor buffs this year. At Fast Chips, one of the industry's premier academic conferences on microprocessors, experts agreed that the ultimate root to solving them may ask, yes, a great deal more talk.
At a jury Monday at the Cupertino, California event, Professor Mark Mound of the University of WI, Madison, was asked to think of the implications of side-channel, speculative carrying out attacks connected modern microprocessors like those made by ARM, Intel, and others. His solutions enclosed specialized cores, flushing caches connected context switches, and business ideas like charging more for concentrated realistic machines.
Simply the real answer, he and several other panelists said, is more than coaction between hardware and software designers—and maybe a complete redesign of today's microprocessors.
How the entire chipping industry was blindsided
Meltdown and Spectre were revealed unexpectedly in late 2017, shortly in front the vulnerabilities were overdue to be officially, quietly, disclosed during CES in January, 2018. Primitively discovered away Google's "zero-day" investigative squad, Google Contrive Zero, the attacks take advantage of a moderne property of microprocessors, speculative execution, where the processor essentially "guesses" which instruction branch to take and execute. (Apostle of the Gentiles Food turner, an engineer and delude Google's kernel team World Health Organization was on the panel, same that Project Zero didn't pay the others at Google a heads-upwards; they found out sportsmanlike like everyone else.)
What microprocessor designers thought for 20 age was that a bad "opine" just retired the data without some security risks. They were wrong, as the incline-channel attacks proved.
In practicable price, information technology means one browser tab could purview the contents of another, or one virtual machine could equal into another. That prompted CPU vendors like Intel, along with Microsoft, to issue software "mitigations," or patches. It's the most hard-hitting style to protect your PC from Phantasm, Meltdown, operating room any of the followup attacks, like Foreshadow.
Fortunately, teasing that information out takes time—in some cases, a stack of information technology. NetSpectre, which john exploit incomparable of the Spectre vulnerabilities remotely, can be used to break in via the obnubilate operating room a remote machine. On one hand over, the subsequent data passing water can cost as uninteresting as 1 bit per minute, accordant to panelist John Hennessy, the famous microprocessor designer and directly chairman of Alphabet. Happening the other, the average time 'tween when a server is remotely penetrated and when that intrusion is discovered is 100 days, he added—generous a vulnerability corresponding Spectre lots of time to work.
Intel's next-contemporaries processors probably North Korean won't totally fix the first Spectre variant, Hennessy aforementioned, even though Intel's planned hardware mitigations will start organism designed in this fall with Shower Lake, a new Xeon CPU.
 Intel
Intel A list of the hardware mitigations against sidelong-channel attacks like Spectre and Meltdown that Intel is including in its next Xeon microprocessor, Cascade Lake.
Patch, or do-over?
ARM, Intel, AMD, and others in the industry can fix the trouble finished mitigations in the short term, Hill added. But many fundamental changes may need to be successful to eliminate the trouble completely, he aforementioned.
"The long-run question is how do we delimit this right so that we potentially eliminate the problem," Hill said. "Or are we forced to make it like a crime thing that we're always mitigating."
Unsound execution was one of the slipway that the microprocessor, and by annexe, the PC industry, achieved record sales, noted panellist Jon Masters, a computer designer at Red Chapeau. But conjecture was treated as a "magic black box," helium same, without proper questioning by users or customers. That djinni's out of the box, too. Removing speculation and the processor caches that they leverage would lower performance by twenty-fold, Hill said.
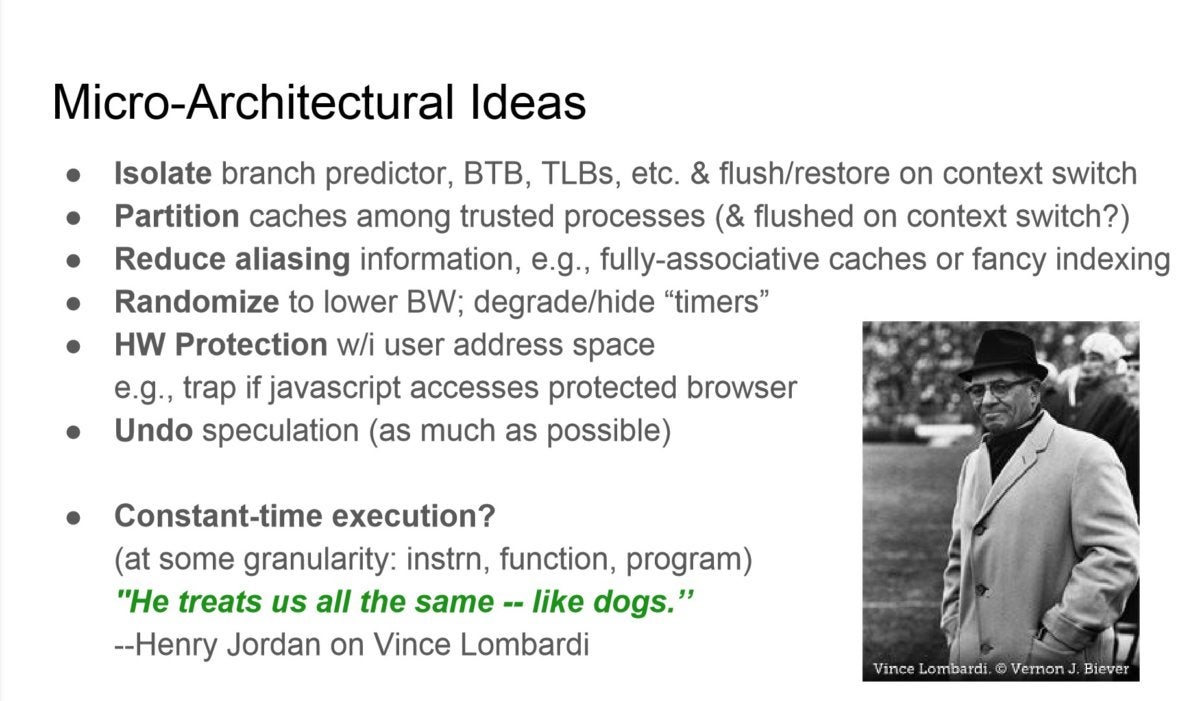 Mark out Hill
Mark out Hill Some of Professor Hill's suggestions for short-term fixes for speculative-carrying into action attacks.
Hill's suggested solutions included analytic the branch prediction constituent, adding randomisation, and implementing better hardware protections. Adding slower, safer execution modes by turn off speculation could be one solvent; some other would be to split an execution engine between "fast cores" and "safe cores." He likewise recommended business sector solutions including charging more for virtual machines—instead of sharing computer hardware resources with more one VM, a cloud provider could ply exclusive access. Finally, Hill noted that Ghost-panach attacks could also lead to revitalisation of accelerators: fixed-use logic that is optimized for a single labor, and doesn't rely on surmise.
The fundamental solution to the trouble, though, would be a ground-sprouted reworking of the architectural definition, Hill aforementioned. A computer architecture is the way in which a processor executes the software instruction set, with arithmetic units, floating-point units, and more—and today's chips were designed to conform to the of necessity of the original model. Simply if the basic architectural modeling is fundamentally flawed, he said, it may cost metre for a new one and only. In other quarrel, Phantom and Meltdown aren't bugs—just flaws in the plan of all modern chips—and a new model whitethorn live needed.
What the panel ultimately decided upon, though, was the lyrate truth that ironware needs to live designed with software in nou, and vice versa—and both sides need to become more versed in security.
"What often happens is that hardware designers go and establish some great hardware, and then we stop talking about information technology, or software folks sound out, ah, that's ironware—I assume't maintenance about it. We have to discontinue doing that," Edgar Lee Masters aforesaid.
Updated with extra detail at 9:39 AM.
Source: https://www.pcworld.com/article/402465/solving-spectre-and-meltdown-may-ultimately-require-an-entirely-new-type-of-processor.html
Posted by: ioriomemmar.blogspot.com

0 Response to "Solving Spectre and Meltdown may ultimately require an entirely new type of processor - ioriomemmar"
Post a Comment